
Android App Spy on Users (EN - 1000 WORDS)
Keypoints:
- Researchers discovered a trojanized Android app, iRecorder - Screen Recorder, with over 50,000 installs on the Google Play store.
- The app initially had no malicious functionality but was later updated with malicious code, potentially indicating involvement in an espionage campaign.
- The malicious app could extract microphone recordings and steal files with specific extensions, raising concerns about user privacy and data security.
I s Your Privacy at Risk? Unveiling the Secret Malicious Code in a Popular Android App.
ESET researchers have discovered a trojanized Android app that was available on the Google Play store with over 50,000 installs.
The app, named iRecorder - Screen Recorder, was initially uploaded to the store without any malicious functionality on September 19th, 2021. However, it appears that malicious functionality was later implemented, most likely in version 1.3.8, which was made available in August 2022.
The Background of the Research
As a partner of the Google App Defense Alliance, the researchers detected a trojanized app available on the Google Play Store, and we named the AhMyth-based malware it contained AhRat.
Initially, the iRecorder app did not have any harmful features. What is quite uncommon is that the application received an update containing malicious code several months after its launch.
The specific malicious behavior of the application, which involves extracting microphone recordings and stealing files with specific extensions, potentially indicates its involvement in an espionage campaign.
The malicious app with over 50,000 downloads was removed from Google Play after our alert; the company have not detected AhRat anywhere else in the wild.
It is rare for a developer to upload a legitimate app, wait almost a year, and then update it with malicious code. The malicious code that was added to the clean version of iRecorder is based on the open-source AhMyth Android RAT (Remote Access Trojan) and has been customized into what we named AhRat.
Besides this one case, the researchers have not detected AhRat anywhere else in the wild. However, this is not the first time that AhMyth-based Android malware has been available on Google Play; we previously published the research on such a trojanized app in 2019. Back then, the spyware, built on the foundations of AhMyth, circumvented Google's app-vetting process twice, presenting itself as a malicious app providing radio streaming.
Overview of the App
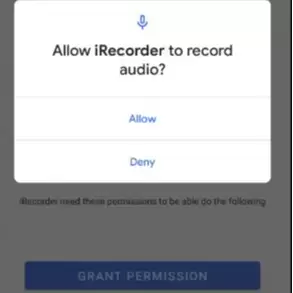
Apart from providing legitimate screen recording functionality, the malicious iRecorder can record surrounding audio from the device's microphone and upload it to the attacker's command and control (C&C) server.
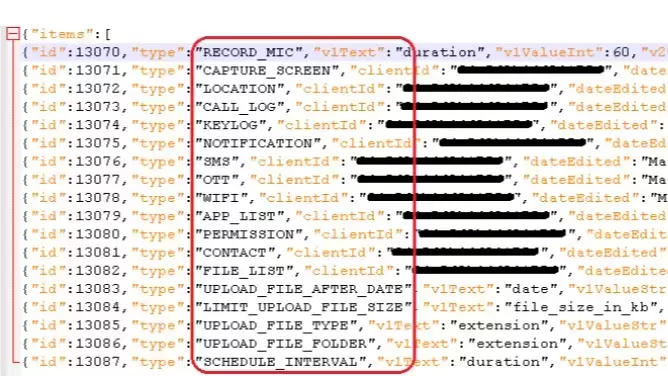
It can also exfiltrate files with extensions representing saved web pages, images, audio, video, and document files, as well as file formats used for compressing multiple files, from the device. The app's specific malicious behavior – exfiltrating microphone recordings and stealing files with specific extensions – tends to suggest that it is part of an espionage campaign. However, we were not able to attribute the app to any particular malicious group.
As a partner of the Google App Defense Alliance, ESET identified the most recent version of the application as malicious and promptly shared its findings with Google. Following our alert, the app was removed from the store.
Distribution
The iRecorder application was initially released on the Google Play Store on September 19th, 2021, offering screen recording functionality; at that time, it contained no malicious features. However, around August 2022, we detected that the app's developer included malicious functionality in version 1.3.8. As illustrated by March 2023, the app had amassed over 50,000 installations.
Attribution
Previously, the open-source AhMyth was employed by Transparent Tribe, also known as APT36, a cyberespionage group known for its extensive use of social engineering techniques and targeting government and military organizations in South Asia. Nevertheless, we cannot ascribe the current samples to any specific group, and there are no indications that they were produced by a known advanced persistent threat (APT) group.
Analysis
During our analysis, ESET identified two versions of malicious code based on the AhMyth RAT. The first malicious version of iRecorder contained parts of the AhMyth RAT's malicious code, copied without any modifications.
The second malicious version, which we named AhRat, was also available on Google Play, and its AhMyth code was customized, including the code and communication between the command and control (C&C) server and the backdoor. As of the time of this publication, we have not observed AhRat in any other Google Play app or elsewhere in the wild, with iRecorder being the only app that has contained this customized code.
AhMyth RAT is a powerful tool capable of various malicious functions, including exfiltrating call logs, contacts, and text messages, obtaining a list of files on the device, tracking the device's location, sending SMS messages, recording audio, and taking pictures. However, we observed only a limited set of malicious features derived from the original AhMyth RAT in both versions analyzed here.
These functionalities appeared to fit within the already defined app permissions model, which grants access to files on the device and permits the recording of audio. Notably, the malicious app provided video recording functionality, so it was expected to ask for permission to record audio and store it on the device.
Upon installation of the malicious app, it behaved like a standard app without any special extra permission requests that might have revealed its malicious intentions.
Preventative Measures and Safeguarding
Fortunately, preventative measures have been implemented in Android 11 and higher versions through App hibernation. This feature places dormant apps in a hibernation state, resetting their permissions and preventing malicious apps from operating as intended. While these measures provide a layer of protection, it is crucial for users to employ additional security solutions like ESET Mobile Security to safeguard their devices against potential security breaches.
AhRat is a customization of the open-source AhMyth RAT, indicating a significant investment of effort by the app's authors. By adapting the code to suit their needs, they gained remote control capabilities over compromised devices, enabling the malicious actions of recording audio and stealing specific file types. The motivation behind these actions, however, remains unknown.
The AhRat app research serves as a stark reminder of the evolving threats in the digital landscape. Users must remain vigilant and prioritize their data protection. Collaborative efforts between security researchers, app stores, and users themselves are crucial in detecting and eliminating such threats. As technology advances, it is imperative to continuously update security measures to stay one step ahead of malicious actors and safeguard the digital ecosystem.
Share Share Share

@1
22 days ago20
@1
22 days ago20